Who are you?
 Identity theft can be devastating for both individuals and companies. Matt Nicholson finds out how you can combat it.
Identity theft can be devastating for both individuals and companies. Matt Nicholson finds out how you can combat it.
This article originally appeared in the Spring 2013 issue of HardCopy magazine.
1958 saw the publication of a short novel by science fiction writer Algis Budrys called Who? in which a Cold War scientist by the name of Dr Lucas Martino is caught in a devastating explosion at a secret research centre. He is ‘rescued’ by the Soviets who, in response to increasing diplomatic pressure, return him to the Americans several months later. However the man they return has undergone not only lengthy interrogation but also extensive surgery, to the extent that he is now unrecognisable. The rest of the book is devoted to the efforts taken by intelligence agent Shawn Rogers to determine whether this is actually Martino, who is vital to the Allied war effort, or a Soviet spy impersonating Martino, in which case he needs to be kept well away from Martino’s work. The task proves extremely difficult.
Although written over 50 years ago, the novel goes to the heart of an increasingly important problem: how we establish and protect our electronic identity. For most of us the solutions we adopt are laughably insecure, but the effects of identity theft can be absolutely devastating.
In August 2012 Mathew Honan, a journalist at Wired.co.uk, experienced them first-hand. It started with his iPhone powering down and then refusing to recognise him when it booted up. Within just a few minutes his iPad and the hard disk of his MacBook were remotely wiped using the Apple iCloud ‘Find My’ service, his Google email account deleted, and his Twitter account hijacked. In the process, he lost more than a year’s worth of irreplaceable photographs.
As a journalist, Honan was able to get to the bottom of how this had happened, and even communicate with one of the hackers. It turned out that high-powered software was not involved. Instead the hackers had used simple search techniques to uncover enough personal information to convince AppleCare to issue a new password – basic information such as an email address, a billing address, and the last four digits of his credit card (which is printed on most receipts). This gave the hackers access to his iCloud account, from which the rest followed. Honan admits in hindsight that he made some basic mistakes that made the hack possible, but his report concludes, “I’m also upset that this ecosystem that I’ve placed so much of my trust in has let me down so thoroughly.”
The underlying problem is that the more effective the password, the harder it is to remember. In these days of cheap computing power, the only effective passwords are those made up of a nonsensical combination of not only upper and lower case letters but also numbers and even punctuation marks. As a result we either write complicated passwords down, usually on bits of paper that are openly visible to colleagues and visitors, or we choose something easy to remember but hopelessly inadequate. An annual study by SplashData, reported in the Daily Mail, reveals that the most popular passwords in 2012 continued to be password, 123456, abc123, qwerty, monkey and letmein.
Sometimes we don’t even bother to use password protection when it’s offered. The recent phone hacking scandal, for example, did not in the main revolve around journalists employing high-powered hacking tools to break into the voicemail services of their targets. Voicemail can be accessed very easily if you know the target’s mobile phone number together with a PIN supposedly known only to the phone’s rightful owner. Most phones are issued with a default PIN which the instruction book advises you to change to something of your own choosing at the earliest opportunity. However few of us bother to read the instructions and so the PIN remains set to its default value which is easily discoverable, and indeed may well be listed on the mobile phone company’s Web site.
Secure solutions
Any authentication procedure boils down to three factors: something you know, such as a password or a PIN; something you have, such as a passport or a key; or something you are, such as a fingerprint or an iris scan. This goes to the heart of Rogers’ problem as anything Martino may have known could have been extracted during his interrogation, and anything he had would certainly have been confiscated. These days we might be able to confirm his identity through genetic fingerprinting, but such technologies weren’t an option 50 years ago.
The more factors employed the more secure the system, so two-factor authentication (TFA or 2FA) is inherently more secure than a single factor solution involving just a password. At present biometric solutions, such as those based on fingerprints or iris scans, tend to be more expensive and less reliable, so most TFA solutions are based on you not only knowing a password but also proving that you have in your possession a particular physical device, usually referred to as an authenticator or token. We use TFA every time we put a debit card (the authenticator) into a cash machine and enter our PIN.
 Authenticators can be either hardware or software. A typical hardware solution involves a small gadget with a button and a digital display. In addition to your PIN you have to enter the number displayed by the gadget when you press the button, so proving that you have it in your possession. This number is referred to as a one-time password (OTP) because it can only be used once. The gadget generates a different number each time in either a unique sequence (event-based), or as a result of a calculation that involves the time at which the button was pressed (time-based). The authenticating software knows how the OTP was generated and so can validate the user, although it does have to allow for accidental button presses or clocks that might not be perfectly synchronised. It is usual for time-based OTPs to remain valid for a certain period, for example.
Authenticators can be either hardware or software. A typical hardware solution involves a small gadget with a button and a digital display. In addition to your PIN you have to enter the number displayed by the gadget when you press the button, so proving that you have it in your possession. This number is referred to as a one-time password (OTP) because it can only be used once. The gadget generates a different number each time in either a unique sequence (event-based), or as a result of a calculation that involves the time at which the button was pressed (time-based). The authenticating software knows how the OTP was generated and so can validate the user, although it does have to allow for accidental button presses or clocks that might not be perfectly synchronised. It is usual for time-based OTPs to remain valid for a certain period, for example.
A variation adds a USB connector to the device so that you don’t have to actually enter the OTP yourself. Instead you plug it into your laptop or desktop and simply enter your PIN, which is automatically combined with the OTP generated by the authenticator before being submitted. Such devices can include encrypted storage which is unlocked once you are authenticated.
Increasingly popular are software authenticators that run on smartphones, many of which can be downloaded free of charge. Google Authenticator is available for Android, iOS and Blackberry, for example, or there is the Authenticator app for Windows Phone 7. Software authenticators are also available for Windows or Mac OS X which are designed to run on a laptop or desktop. With these the second factor – the thing you have as opposed to the thing you know – becomes the laptop or desktop itself.
The authenticators described so far require hardware or software that is in the possession of your users. This can pose a security risk if these are temporary workers or contractors as you have to ensure that they hand back or uninstall their authenticators when their time with you is finished. Here a more suitable solution might be an out-of-band (OOB) authenticator where the user is sent an SMS or an email containing the OTP. This is managed from the server and doesn’t require any specialist software or hardware for the user.
The other important component in a TFA system is the in-house system where authenticators are registered and managed. Most of the major suppliers have authentication managers that run on Windows Server. Quest Defender, for example, is built on top of Active Directory and can be managed either through a Web browser or an MMC (Microsoft Management Console) plug-in. RSA Authentication Manager, as supplied by EMC which acquired RSA in 2006, is available not only for Windows Server but also for Red Hat Enterprise Linux and 64-bit Solaris. EMC can also supply RSA Authentication Manager Express, a rack-mountable box that is designed for companies with up to 2,500 users. Another option is the SafeNet Authentication Service which can be delivered both as an Enterprise Cloud Service and in a Private Cloud Edition.
SafeNet supports the Initiative for Open Authentication (OATH) which means its authentication products will work with any OATH-compliant authenticator. Quest Software also supports OATH which means that any SafeNet authenticator can be managed by Quest Defender, as indeed can Google Authenticator and Authenticator for Windows Phone 7, which are also OATH compatible.
One company that does not support OATH is EMC. Its RSA products uses techniques which EMC argues are stronger than OATH’s, and also points out that an initiative like OATH can only be as secure as the weakest link in the supply chains of member organisations.
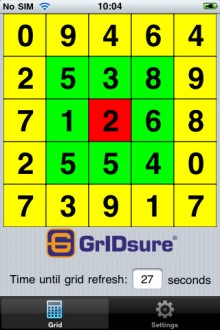
The GriIDsure authenticator in action on a mobile device – gain entry by typing the digits that match your chosen pattern.
Another option is the GrIDsure authenticator. To register with a GrIDsure system the user chooses a pattern of cells from within a grid. When it comes to authentication the user is presented with a grid populated by a random set of digits (see previous page), and he then enters the values displayed in the cells that match his chosen pattern. The user’s pattern remains the same, but the values he enters are different every time. GrIDsure was liquidated in 2011 and its patents acquired by Cryptocard, which is now part of SafeNet. The technology is licensed to other companies including Quest.
A recent development is risk-based authentication. This involves evaluating the risk posed by each authentication attempt and adjusting the procedure accordingly. A log-in from a laptop in the company canteen, for example, is a rather less risky proposition than a log-in from a smartphone connected to the public Wi-Fi system of a hotel in another continent. A risk-based system makes an evaluation according to known information, perhaps allowing the user in the canteen to log in with a simple password while requiring the smartphone user to also enter a OTP. Risk-based system are available from a number of suppliers including RSA and CA Technologies.
Although TFA solutions represent a considerable investment, they can still prove cost effective. For a start, the Help Desk Institute has stated that nearly a third of all help desk calls are requests for password resets. Then there is the potentially enormous cost incurred by a security breach, which could easily extend into the millions, to say nothing of the loss of trust and the damage to your reputation.
Password managers
That said, there are many situations where passwords are the only option, in which case it makes sense to ensure that they are as secure as possible. This is particularly important given the computing power available to the hacker. A four-digit PIN can take one of only 10,000 values which the modern desktop can crack in a matter of milliseconds. Just a few minutes searching the Web will reveal toolkits for recovering smartphone PINs that come with friendly user interfaces and require no understanding of what they’re actually doing behind the scenes.
To be really effective a password needs to be made up of at least eight random characters which can be both numbers or both upper and lower case letters, so presenting the hacker with some 218 trillion possible combinations. Furthermore you should use a separate and unrelated password for each system that you need to access, so that cracking your password for Facebook does not give the hacker access to your bank account. Most of us find it difficult enough to remember more than one such password, so the only realistic solution is to use something that stores all your passwords in a single encrypted database that can only be accessed through a single master password.
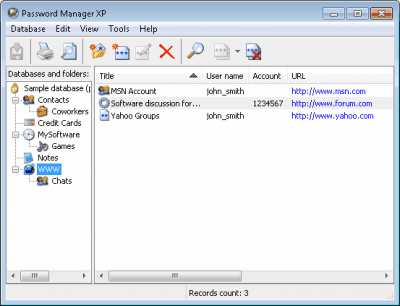
Password Manager XP from CP Lab gives you a secure place to store and manage your login details.
A typical example is Password Manager XP from CP Lab which can store not only usernames and passwords but also credit card details and other confidential information. It can be set up to auto-fill Web pages and log-in dialogs, entering account details and passwords directly into the correct fields without you having to copy-and-paste or type them in, which can defeat the key-logging software used by hackers. It can automatically generate passwords that have a high degree of security, so removing the need for you to dream up nonsensical character strings. It also supports multiple users, each with access only to specific parts of the shared database.
Like many such utilities, Password Manager XP comes in a version for smartphones, although in this case only Windows-compatible devices are supported up to Windows Mobile 6.1. It also supports installation to a USB memory stick which gives you access to your passwords in a secure manner from any computer without having to install any software.
A similar package is offered by Moon Software in Password Agent. This does not support multi-user access or smartphones, but it can be installed on a USB drive. It also comes in a free Lite version that offers all the features of the full version but limited to just 25 entries. Then there is KeePass, an open source alternative that is available not only for Windows but also for Mac OS X and other UNIX variations including Linux. There are also variants such as MiniKeePass for iOS, KeePassDroid for Android and 7Pass for Windows Phone 7.
There are quite a number of password managers available for smartphones, however forensic expert ElcomSoft has reported that few make use of the facilities provided by their target platforms for securing passwords, preferring to ‘roll their own’ which are inherently less secure. One that did come out well is Ascendo DataVault which supports Android, iPhone, iPad and Blackberry, as well as Mac OS X and Windows (but not Windows Phone).
However it is important to remember that none of these tools will prevent a hacker from persuading a call centre to reset your password if they have access to the right information. Far more important is that you take precautions to protect your personal data – information such as your date of birth, your mother’s maiden name, your billing address. Foregoing a few birthday greetings on Facebook is a small price to pay if it avoids the nightmare of identity theft.
Coding for security
Techniques for developing a secure application or Web site could fill several books (and indeed have). However here are a few tips:
-
Modern development platforms support a wide range of security features that have been extensively tested. Don’t be tempted to roll your own.
-
No matter what anyone advises, people continue to use the same password across multiple sites, so take security seriously even if your particular application is relatively trivial.
-
Never store passwords in plain sight. Most development platforms support strong encryption, but at the very least you should concatenate each password with a random string before hashing (the nature of hash algorithms means that you can store each string alongside the hash without compromising security).
-
Many Web development platforms maintain an illusion of flow through the application. However the Web is stateless so test whether the user is authenticated on every page.
-
Validate any data entered by the user before passing it on to the application, and only allow the application to access a database through stored procedures.
For more on this subject see my article Writing secure code elsewhere on this site.
Find out more
ElcomSoft’s report is available at www.elcomsoft.com/PR/PK_120316_en.pdf. Further details of many of the products mentioned here can be found on the Grey Matter Web site at www.greymatter.com. If you would like to discuss your security needs further then call Grey Matter on 01364 654100 or email maildesk@greymatter.com.

Hi Matt
Thanks for writing this. I had my laptop stolen last summer, which had two effects: (1) I couldn’t remember all those logins and passwords I had ‘asked it’ to remember for me and (2) I realised that if it could ‘remember’ them for me, then the laptop in someone else’s hands might be able to let them into my accounts too. Thankfully that didn’t happen, but it did make me re-think my entire strategy towards passwords. I’d already started to use more secure passwords, which was where the memory problem came in. Now I use one of those password managers you mention, in my case, 1password. It works on all my devices, phone, tablet and laptop. In my case those are all Apple, but 1password is cross-platform, and I recommend it.
It took me a few days to work through all my usual accounts, logging into them and allowing 1password to store the user id and password. I let it generate new maximum security passwords for the the important ones (and have since done it for them all). Now I only have to remember one password, which allows me into 1password itself, and from there I can get into any of my accounts on any of my devices. Granted, it is easiest on the laptop itself, where there is a toolbar button in the web browser, which I click on whenever a log-in screen appears. It allows me to ‘fill’ the fields with the details 1password has stored. Whenever I register for a new site, I can ask it to generate a suitable password, and then store it.
Do I trust 1password? I did look into this. They have been in the business some time and security IS their business, so their reputation depends on maintaining security. The data is stored (encrypted of course) on your own hard disk, although it is also stored in Dropbox to allow it to be used on other devices. But I haven’t come across a better solution to the problem I had.
Another bit of advice I have heard recently is to lie when setting up answers to security questions. However, you need to be able to recall the answers when necessary. 1password allows you to store notes, so here you can note down all those fake mother’s maiden names and first schools you didn’t go to.
Cheers
C.
LikeLike
Having written this article I now use KeePass in conjunction with Dropbox, which is very similar to your solution. It does seem to work very well. I have also started using your technique of faking mother’s maiden names and birthdays. A friend of mine used to do this with his address years ago, using different spelling variations each time he was asked to supply it. As a result he was able to check who was responsible for the junk mail he received through the post. Where will it all lead, I wonder?
LikeLike
Well, assuming that in hundreds of years’ time they can still read our records (which is currently unlikely – see Charles Stross, Glasshouse, a novel based on this premise), it will be a nightmare for historians trying to work out just who our mothers were and where we were educated! (:-)
LikeLike
Seriously though (now I have a ‘gravatar’ for my profile), I find it difficult to get my head round what is and is not a good thing to do security-wise. We could not resist getting a domain name with our house name in it. The trouble is, you only have to Google the house name and right there at the top of the list is the whole address, which is, of course, my usual billing address. So I’m not sure what I’m going to use the domain for, other than to park ‘test’ web sites that are not actually identifiable with me (I used to use Mobile Me for this but Apple pulled the plug on that). Except that I can’t even be sure that this is safe.
By the way, there is a forestperson in the picture, but it’s not me.
LikeLike
Like the gravatar picture! Security is a difficult one. The important point to remember is that you are in much the same position as a group of people being chased by a lion: you don’t have to be the fastest – you just need to outrun the slowest. When we moved in to the house we lived in now, we had no intention of getting a burglar alarm. However, when all our neighbours did, we had no option but to install one ourselves – otherwise we’d have been the only house without one.
LikeLike
Well as it’s not me, you may be able to guess who it is in the picture. Unfortunately neither Simon, nor my mother, nor Richard took/take pictures of me when we were/are out walking, so most of my photos of ‘forest people’ are of them. I like the lion image. I’ll remember that.
LikeLike